Generally, the trusted domain contains the users, while the trusting domain contains the resources. Therefore, users from the trusted domain will be able to access resources in the trusting domain because the users are trusted. Trusts can be created automatically or manually. Trusts can also be classified as transitive and non-transitive. Transitive trust simply means that if Domain A trusts Domain B and Domain B trusts Domain C, then Domain A trusts Domain C. Similarly with non-transitive trusts, if Domain A trusts Domain B and Domain B trusts Domain C, then Domain A does NOT trust Domain C. Also, trusts can be one-way or two-way. Different types of trusts described below are either one- or two-way by default.
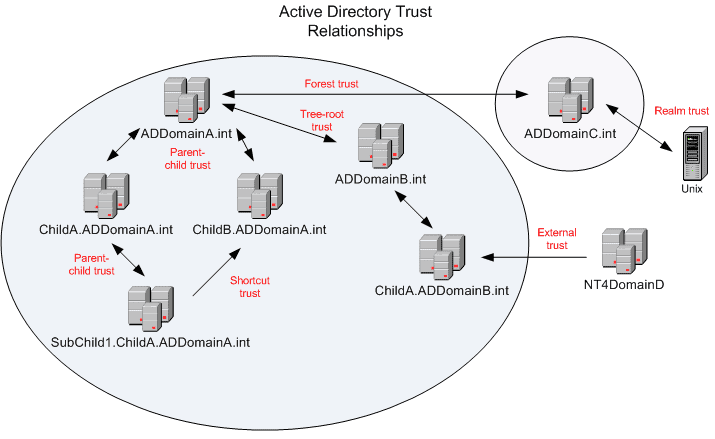
Tree-root trust
A tree-root trust is implicitly established when you add a new tree root domain to a forest. The only domains that participate in the tree-root trust are those at the top of each of the trees. Tree-root trusts are two-way transitive trusts created automatically.
Parent-child trust
A parent-child trust relationship is implicitly established when you create a new child domain in a tree. The DCPromo process automatically creates a trust relationship between the new domain and the domain that immediately precedes it in the DNS namespace hierarchy. Parent-child trusts are two-way transitive trusts created automatically.
Shortcut trust
A shortcut trust must be explicitly created by a system administrator between two domains in the same forest. This type of trust is typically used in large forests where the administrator would manually create this type of trust to improve user logon time for those users that logon to computers in another domain within the forest. This type of trust is transitive and can be configured as one- or two-way.
External trust
An external trust must be explicitly created by a system administrator between two domains in different forests, or between a domain in an Active Directory forest and a Windows NT 4.0 or earlier domain. This trust is very useful when migrating resources from a Windows NT 4.0 domain to one within an Active Directory domain. This type of trust is non-transitive and can be one- or two-way.
Forest trust
A forest trust must be explicitly created by a systems administrator between two forest root domains (Windows 2003 and later). This trust allows for all domains in one forest to transitively trust all domains in another forest. However, this type of trust is not transitive over three or more forests. Forest trusts can be one-or two-way. Forest trusts are only available when the forest functional level is set to Windows Server 2003 or later.
Realm trust
A realm trust must be explicitly created by a systems administrator between a non-Windows Kerberos realm and a Windows 2003 or later domain. This type of trust can be transitive or non-transitive and one- or two-way. The most important component in regards to trust relationships is the proper planning to ensure that users are provided with the access to resources that they require.